PROFESSIONAL
Software Solutions
Hardware Solutions
Dedicated Server
IT Products
|
Sevengate is a value-added distributor and professional services provider based in Amman, Jordan and founded in 2007.
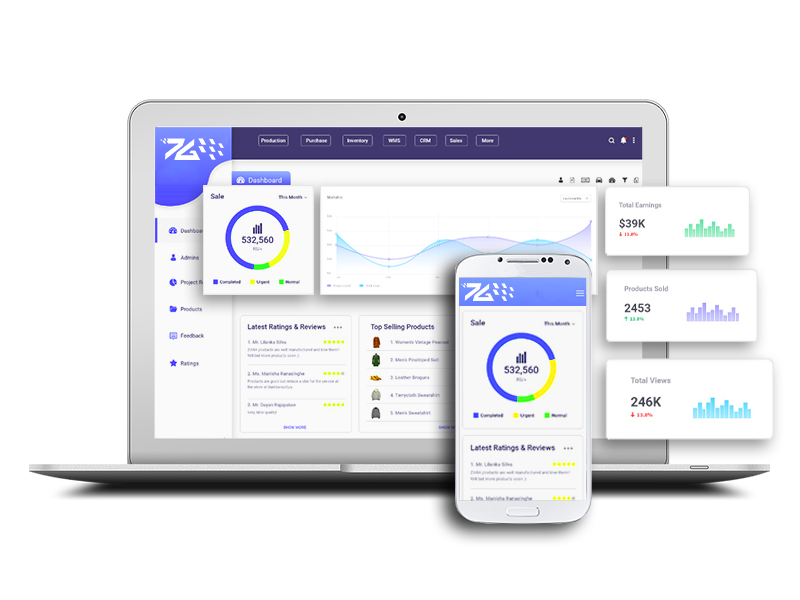





IT Solutions
Hardware/Software Solutions
Sevengate providing for you a professional services in IT products.
Build your company identity, Software Applications, Networks Implementation, Security as well as 24/7 Technical Support.


OUR PRODUCTS
PROFESSIONAL IT PRODUCTS

For the hard-working people in the world’s most demanding industries, ...
No matter your business and offering—service provider, hyperscaler, ...

Dahua Technology is a world-leading and advanced video ...

ESET Internet Security
ADVANCED SECURITY 2023 EDITION. ...

The modern beleaguered CISO has to balance the challenges of ...

Forcepoint is the leading user and data security cybersecurity company, ...

Sangfor Technologies is a leading global vendor of IT infrastructure solutions, ...

From ransomware and insider threat, to business email compromise and ...
- Training
- Professional Services
- Managed Security Services
- Consultancy
Training
Sevengate gives high attention and focus on training quality and employs certified instructors who specialize on the most well recognized security products in the market ….
TRAINING
Sevengate gives high attention and focus on training quality and employs certified instructors who specialize on the most well recognized security products in the market. Sevengate also acts as a certified training partner for Sophos security solutions.
Sevengate provides training for the below security subjects:
SCSE [Sophos Certified Security Engineer] certification course prepares individuals to recognize insider threats and user-targeted external threats while giving them expertise in networking and security fundamentals in addition to the deployment and configuration of Sophos Next Generation Firewalls.
The course is comprehensive, yet easy to follow, with real world scenarios, delivering practical value to aspirant security professionals.
SCSA [Sophos Certified Security Architect] certification course is meant for SCSE-certified professionals to advance their career.
It provides them with the expertise in deploying Sophos security in complex scenarios for enterprise networks. Course participants will learn about advanced debugging and troubleshooting issues and deepen their understanding of Sophos security architecture.
Hands-on lab sessions allow participants to gain direct exposure to events that take place in a Sophos enterprise set-up, product installation, integration into a network, configuration for various Sophos features such as anti-virus, anti-spam, content filtering, VPN, IPS, high availability etc. and support / troubleshooting issues.
SCT [Sophos Certified Trainer] is a certification program that trains and certifies SATP [Sophos Authorized Training Partners] and Sophos Authorized Distributors to become certified trainers for Sophos certification programs. The program is meant for partners who hold a Learning Solutions competency and who have demonstrated an exceptional knowledge of Sophos range of products and maintain technical and instructional expertise using Sophos Next Generation Firewalls.
The SCT program fulfillment allows Sophos Distributors or Authorized Training Partners and individuals to impart Sophos professional level certification programs.
If you are interested to get Sophos training please register at training@sevengatellc.com
Professional Services
Passive Networks Implementation
We implement and deliver structured cabling designs and installations, governed by international ….
PROFESSIONAL SERVICES
Passive Networks Implementation
We implement and deliver structured cabling designs and installations, governed by international standards and categories to guarantee secure and scalable networks, ranging from small offices up to datacenter and campuses. Our structured cabling designs allow multi-layered applications to run efficiently and integrate seamlessly with any active components with minimum loss of bandwidth and capacity. Moving forward and ahead of others in the market PON concept which adds more winning strategies is added to our product portfolio, this will allow more expansion for network capacity, coverage and convergence with composite experience of passive and active networking at the physical & L2 level.
Network Design and Planning
Each network has its unique and proprietary design to cope with the ever changing business needs. We believe in the converged network proposition concept a key of reducing CAPEX/OPEX and TCO in best means of planning and design to guarantee the best ROI also to reduce any negative influence on long-term or short-term projects as well as operations and maintenance. Sevengate network team has an accumulative experience in active components configuration, design and planning.
Network Upgrading
Business continuity and up to date integrity is what we aim to achieve, Sevengate IT professionals are strongly trained on insuring minimum downtime operation during the upgrade and expansion phase or during network reengineering, they succeed to accommodate new employees and new IT network components or system integration seamlessly without affecting business or network performance.
Network Security
Sevengate security solutions protect network inbound and outbound traffics using Next Generation Firewalls that work on the Human Layer, delivering a real-time protection against external and internal threats ranging from small and remote offices up to large enterprise clients.
The security solutions that are used help IT managers to get a secure networks by protecting all network layers and levels, it is capable to handle L2 toL7 traffics in various network scenarios also handle Internet security, web servers, web applications, mail security and gateway traffic monitoring using a unified affordable and easy to use solution without compromising security or performance.
Unified Communication
Unified communication simplifies collaboration and gives reliable voice communication, fully integrated video conferencing, mobility, Tele-Presence and more.
We deliver IP based unified communication systems which are easy to use and guarantee five nines availability.
Wireless Networking
Today WiFi is a must have technology and became a popular trend and necessity to all kind of users.
Apart from having a standalone AP deployment we managed to push centralized network controller technology to the market using the best of breed products and professional integration with the network operation center (NOC), this concludes to a paradigm shift of mobility and security principle.
We assure that our solution keeps you unplugged but well connected.
Backup and Recovery Services
Backup solutions safeguard the digital assets economically for decades and grants instant access as needed.
Our data backup software and appliances protect physical, virtual, and multi-platform server environments including remote and branch offices in an agile mechanism built on proven, disk-based technology.
Cloud Backup provides redundant storage, ensured uptime, and guaranteed security even endpoint files are available from anywhere at any time. Backup and recovery boost user productivity and network performance with cloud or onsite recovery setups.
Surveillance Secure Systems
CCTV is a tangible demonstration tool in the fight against crime, terrorism assists with detection. CCTV equipped areas are less attractive target if an offender is aware about this security feature. Monitoring suspicious behavior also gives organizations greater ability to protect their properties and the public from harm.
Managed Security Services
“Identify threats as they occur”
we provide full management and 24/7 monitoring for a wide range of systems ….
MANAGED SECURITY SERVICES
“Identify threats as they occur”
we provide full management and 24/7 monitoring for a wide range of systems.
Sevengate offers a hassle free experience of managing the on-premise customer Firewalls.
We provide round-the-clock protection and monitoring of your systems, whatever your business is.
This is an unmatched security service offering which grants you peace of mind and solid protection.
Subscribe today for supervised security infrastructure and peace of mind.
Why Use this Service:
– Monitor your device log, data events.
– Easy configuration and administration.
– Conduct 24/7 devices health check.
– Comprehensive and analytic reports.
– Remotely installs security devices patches, and software upgrades.
Consultancy
Enterprises and SMBs have unique needs that influence their technology decisions; they both share the need for a well-managed and secure network and infrastructure which is meant to be reliable, secure, ….
CONSULTANCY
Enterprises and SMBs have unique needs that influence their technology decisions; they both share the need for a well-managed and secure network and infrastructure which is meant to be reliable, secure, interoperable and upgradable to retain business and to cope with the ever changing demand for new technologies.
Defining business needs requires understanding of various levels of platforms, applications, and hardware in the company as well as the data volumes generated throughout the organization.
Sevengate consultancy services and solutions map all what it needs to guarantee simple, flexible and cost effective solution with best ROI value.
Selecting the best solution that fits your business needs is one of Sevengate scopes. We work with international organizations and agencies to deliver different solutions covering different subjects and levels to serve clients.
Sevengate consultation services allow growth and rapid developments for new technologies without causing complexity, inflexibility or forklift upgrades regardless of business requirements or network environments, also address the complex and ever-changing IT environment of enterprises or SMBs and provide consultation services for a better optimized solutions.
Sevengate consultation services cover the following subjects:
– Implementation of data centers
– Building scalable enterprise network infrastructure
– Web applications management and planning
– Bandwidth management & network resources planning
– Policy enforcement firewall design and configuration
– ISP traffic management and monitoring
– Managing inbound and outbound traffics
– Security design for virtualized environments
– Server farm management and load balancing
– Unified communication planning
– Cloud backup for virtualized environments
– Threat management and MSS
– NAC for the enterprise
– End point data protection
Training
Sevengate gives high attention and focus on training quality and employs certified instructors who specialize ....
TRAINING
Sevengate gives high attention and focus on training quality and employs certified instructors who specialize on the most well recognized security products in the market. Sevengate also acts as a certified training partner for Sophos security solutions.
Sevengate provides training for the below security subjects:
SCSE [Sophos Certified Security Engineer] certification course prepares individuals to recognize insider threats and user-targeted external threats while giving them expertise in networking and security fundamentals in addition to the deployment and configuration of Sophos Next Generation Firewalls.
The course is comprehensive, yet easy to follow, with real world scenarios, delivering practical value to aspirant security professionals.
SCSA [Sophos Certified Security Architect] certification course is meant for SCSE-certified professionals to advance their career.
It provides them with the expertise in deploying Sophos security in complex scenarios for enterprise networks. Course participants will learn about advanced debugging and troubleshooting issues and deepen their understanding of Sophos security architecture.
Hands-on lab sessions allow participants to gain direct exposure to events that take place in a Sophos enterprise set-up, product installation, integration into a network, configuration for various Sophos features such as anti-virus, anti-spam, content filtering, VPN, IPS, high availability etc. and support / troubleshooting issues.
SCT [Sophos Certified Trainer] is a certification program that trains and certifies SATP [Sophos Authorized Training Partners] and Sophos Authorized Distributors to become certified trainers for Sophos certification programs. The program is meant for partners who hold a Learning Solutions competency and who have demonstrated an exceptional knowledge of Sophos range of products and maintain technical and instructional expertise using Sophos Next Generation Firewalls.
The SCT program fulfillment allows Sophos Distributors or Authorized Training Partners and individuals to impart Sophos professional level certification programs.
If you are interested to get Sophos training please register at training@sevengatellc.com
Professional Services
Passive Networks Implementation We implement and deliver structured cabling designs and installations, governed ....
PROFESSIONAL SERVICES
Passive Networks Implementation
We implement and deliver structured cabling designs and installations, governed by international standards and categories to guarantee secure and scalable networks, ranging from small offices up to datacenter and campuses. Our structured cabling designs allow multi-layered applications to run efficiently and integrate seamlessly with any active components with minimum loss of bandwidth and capacity. Moving forward and ahead of others in the market PON concept which adds more winning strategies is added to our product portfolio, this will allow more expansion for network capacity, coverage and convergence with composite experience of passive and active networking at the physical & L2 level.
Network Design and Planning
Each network has its unique and proprietary design to cope with the ever changing business needs. We believe in the converged network proposition concept a key of reducing CAPEX/OPEX and TCO in best means of planning and design to guarantee the best ROI also to reduce any negative influence on long-term or short-term projects as well as operations and maintenance. Sevengate network team has an accumulative experience in active components configuration, design and planning.
Network Upgrading
Business continuity and up to date integrity is what we aim to achieve, Sevengate IT professionals are strongly trained on insuring minimum downtime operation during the upgrade and expansion phase or during network reengineering, they succeed to accommodate new employees and new IT network components or system integration seamlessly without affecting business or network performance.
Network Security
Sevengate security solutions protect network inbound and outbound traffics using Next Generation Firewalls that work on the Human Layer, delivering a real-time protection against external and internal threats ranging from small and remote offices up to large enterprise clients.
The security solutions that are used help IT managers to get a secure networks by protecting all network layers and levels, it is capable to handle L2 toL7 traffics in various network scenarios also handle Internet security, web servers, web applications, mail security and gateway traffic monitoring using a unified affordable and easy to use solution without compromising security or performance.
Unified Communication
Unified communication simplifies collaboration and gives reliable voice communication, fully integrated video conferencing, mobility, Tele-Presence and more.
We deliver IP based unified communication systems which are easy to use and guarantee five nines availability.
Wireless Networking
Today WiFi is a must have technology and became a popular trend and necessity to all kind of users.
Apart from having a standalone AP deployment we managed to push centralized network controller technology to the market using the best of breed products and professional integration with the network operation center (NOC), this concludes to a paradigm shift of mobility and security principle.
We assure that our solution keeps you unplugged but well connected.
Backup and Recovery Services
Backup solutions safeguard the digital assets economically for decades and grants instant access as needed.
Our data backup software and appliances protect physical, virtual, and multi-platform server environments including remote and branch offices in an agile mechanism built on proven, disk-based technology.
Cloud Backup provides redundant storage, ensured uptime, and guaranteed security even endpoint files are available from anywhere at any time. Backup and recovery boost user productivity and network performance with cloud or onsite recovery setups.
Surveillance Secure Systems
CCTV is a tangible demonstration tool in the fight against crime, terrorism assists with detection. CCTV equipped areas are less attractive target if an offender is aware about this security feature. Monitoring suspicious behavior also gives organizations greater ability to protect their properties and the public from harm.
Managed Security Services
“Identify threats as they occur”
we provide full management and 24/7 monitoring for a wide range of systems.
Sevengate offers a hassle free experience of ...
MANAGED SECURITY SERVICES
“Identify threats as they occur”
we provide full management and 24/7 monitoring for a wide range of systems.
Sevengate offers a hassle free experience of managing the on-premise customer Firewalls.
We provide round-the-clock protection and monitoring of your systems, whatever your business is.
This is an unmatched security service offering which grants you peace of mind and solid protection.
Subscribe today for supervised security infrastructure and peace of mind.
Why Use this Service:
– Monitor your device log, data events.
– Easy configuration and administration.
– Conduct 24/7 devices health check.
– Comprehensive and analytic reports.
– Remotely installs security devices patches, and software upgrades.
Consultancy
Enterprises and SMBs have unique needs that influence their technology decisions; they both share the need for a well-managed and secure network ...
CONSULTANCY
Enterprises and SMBs have unique needs that influence their technology decisions; they both share the need for a well-managed and secure network and infrastructure which is meant to be reliable, secure, interoperable and upgradable to retain business and to cope with the ever changing demand for new technologies.
Defining business needs requires understanding of various levels of platforms, applications, and hardware in the company as well as the data volumes generated throughout the organization.
Sevengate consultancy services and solutions map all what it needs to guarantee simple, flexible and cost effective solution with best ROI value.
Selecting the best solution that fits your business needs is one of Sevengate scopes. We work with international organizations and agencies to deliver different solutions covering different subjects and levels to serve clients.
Sevengate consultation services allow growth and rapid developments for new technologies without causing complexity, inflexibility or forklift upgrades regardless of business requirements or network environments, also address the complex and ever-changing IT environment of enterprises or SMBs and provide consultation services for a better optimized solutions.
Sevengate consultation services cover the following subjects:
– Implementation of data centers
– Building scalable enterprise network infrastructure
– Web applications management and planning
– Bandwidth management & network resources planning
– Policy enforcement firewall design and configuration
– ISP traffic management and monitoring
– Managing inbound and outbound traffics
– Security design for virtualized environments
– Server farm management and load balancing
– Unified communication planning
– Cloud backup for virtualized environments
– Threat management and MSS
– NAC for the enterprise
– End point data protection
Contact us
Write us a Mail
⬤ info@sevengatellc.com
Make us a Call
⬤ +962 6 556 3596
+962 6 582 0428
Reach us at Office
⬤ Building 17, 2nd Floor,
Hilwani Center Wakalat-St.
Al'Swifieh - Amman - Jordan












